By Carmen Galvan
Assistant City Editor
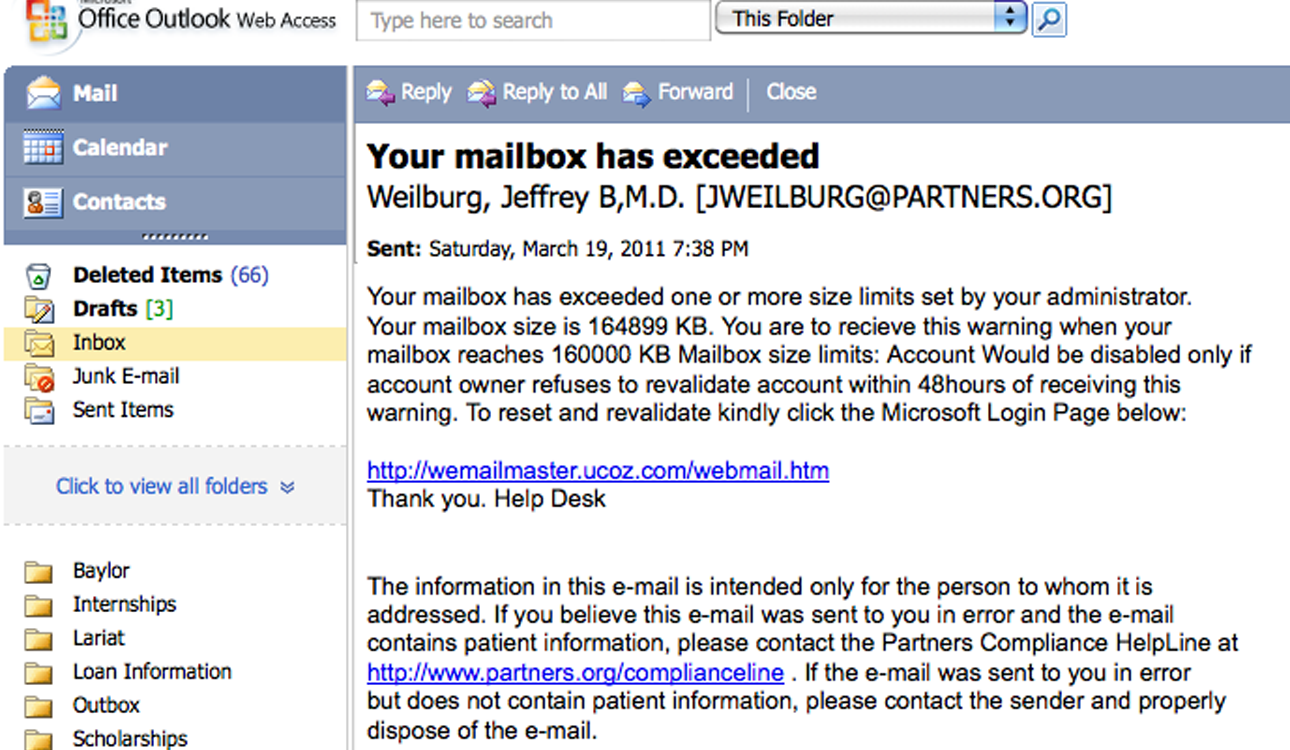
Due to a heavy wave of Internet phishing, Baylor Information Technology Services is cautioning students, faculty and staff to read their email carefully before responding to any requests.
Derek Tonkin, information security analyst for Baylor Information Technology Services said, phishing emails are attempts to trick a user to reveal personal information such as account usernames and passwords, credit card numbers and expiration dates or other information that may be used for economic gain.
The emails are sent from “phishers” who mask their actual email address with those of well-known banks, information technology departments and social networking sites in the hope that users will respond to what they think is a trusted source.
Jon Allen, information security officer for Baylor ITS, said limited networks, like that of a university’s, are often targeted for this type of scam.
“We call it spearing,” Allen said. “They’re targeting a specific organization and you receive specific emails, as in your Baylor webmail is going to expire. It’s very directed and not so generalized like Bank of America where, if you don’t have something from Bank of America, you throw it away.
“The problem we have now is a much more personal connection with the message because it’s targeting an organization, so universities are experiencing this significantly because it’s very easy to identify, like the Baylor.edu email address.”
Tonkin said that once a phisher — who usually belongs to an electronic crime syndicate — receives users’ information, he or she can then scan users’ contact list to send more phishing emails and/or use the information for identity theft.
Tonkin and Allen said that while the university receives approximately 10,000 phishing messages per day, barely 500 of the messages actually reach user mailboxes because of preventative measures the information technology department has put in place. But this doesn’t stop phishers from continually developing new techniques that penetrate information technology safeguards, which then requires the department to quickly develop new measures in order to stop a new wave of phishing emails.
“We see it in waves,” Allen said. “So there will be times where we see a couple hundred come in a day, not a big deal, and there will be times where we will see thousands and thousands. We’re in a wave right now where we see a lot of messages coming in. We have no way to predict that. …The start of the school year is a busier time, we don’t know why, and then there are times of the year where it’s quiet.”
Allen and Tonkin said Baylor is in the middle of such a wave, while no numbers have not been reported, there have been several instances of students replying to phishing emails due to hurried reading and response.
“We do a lot to try to promote and make people aware of this: There’s a sense of urgency to all these messages; it’s one of the keys,” Allen said.
“They’re trying to catch you off guard so that your normal senses that tell you, ‘Don’t do this,’ fall away because you’re kind of panicked at that point. A lot of time they send messages overnight so students see it first thing in the morning while they’re trying to get to class, trying to get ready, and they say, ‘Oh no, I need to fix that, I need access to my email today,’ and then they realize it isn’t Baylor.”
Baylor ITS sends out BearAware alerts in an attempt to block phishing attacks when traffic becomes especially heavy, but Allen encourages people to be wary of potential phishing emails at all times since it is an ongoing problem.
“It’s a constant evolving effort,” Allen said.
“We try to identify new ways [of phishing] and try to block it, but they have just as many, if not more, people working on it. What you block today is different from tomorrow, so you have to block tomorrow. It’s just a race back and forth.”
To prevent users from believing false emails, Allen and Tonkin said authentic Baylor emails will never ask users to click on a link provided and will never ask for a user password via email.
Pattie Orr, vice president for information technology and dean of university libraries, also suggested that students practice caution when accessing and replying to email.
“Be skeptical, be very skeptical,” Orr wrote in an email to the Lariat.
“Being ‘phished’ compromises your privacy and is an inconvenience since your email may need to be disabled for a period of time and you will have to resolve issues with other online accounts.
“If in doubt, don’t click; manually enter the website address for Baylor or the company that sent the email to verify the information or call the Baylor Help Desk for advice or assistance.”
If a user does respond to a phishing email, Allen and Tonkin said to immediately change the account password at www.baylor.edu/bearid as most phishers do not begin using the information until at least a few hours after receiving it.
Users who receive the email are also encouraged to report the phishing attempt to Information Technology Services.